
Traditional perimeter-based security is obsolete. Once inside, attackers move freely. Without continuous verification, trusted accounts become major vulnerabilities.
Implement a Zero Trust architecture with ManageEngine. Enforce strict identity verification, apply least-privilege access, and continuously monitor trust levels for every user and device, inside or outside the network.
Contact Us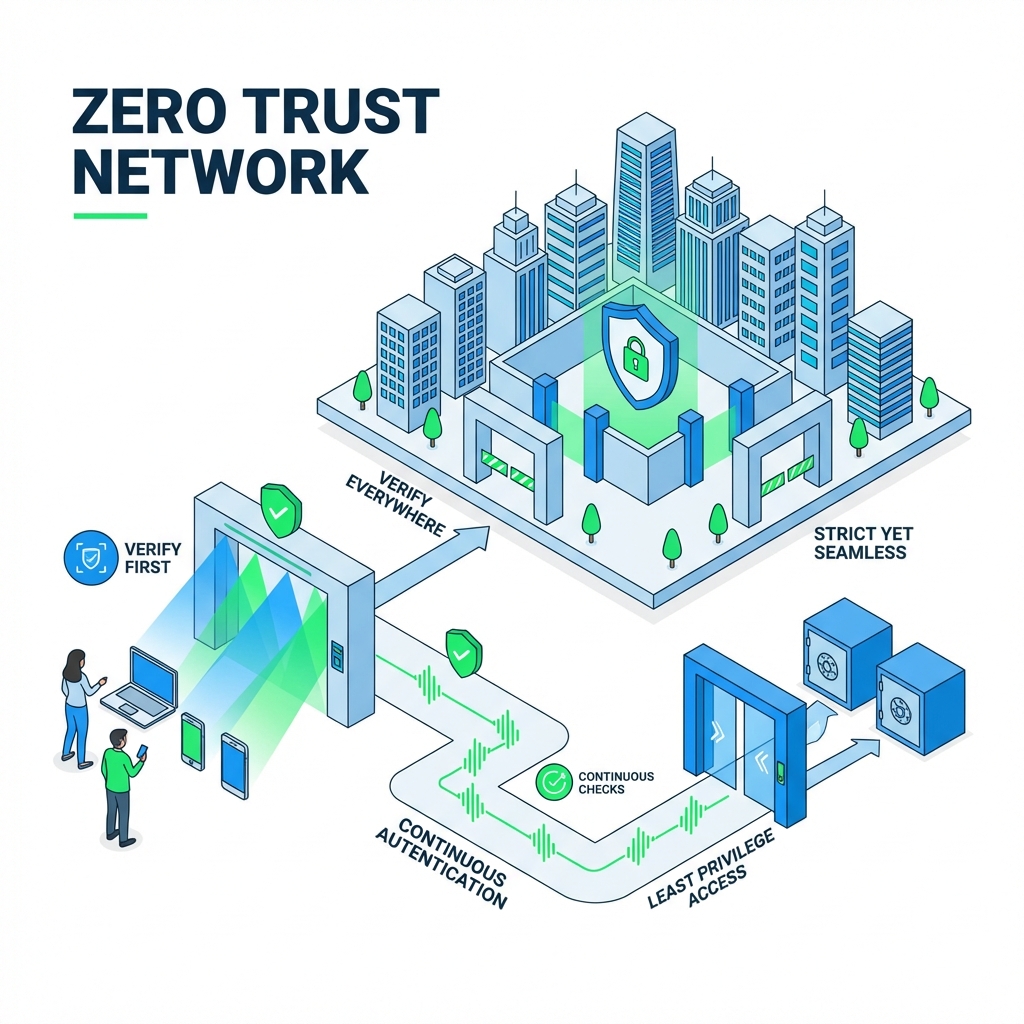
Verify identity at every access attempt with adaptive MFA.
Restrict access to only what is necessary for the user's role.
Limit lateral movement by securing individual resources and data segments.